Powerful Features
Entire Lifecycle Management
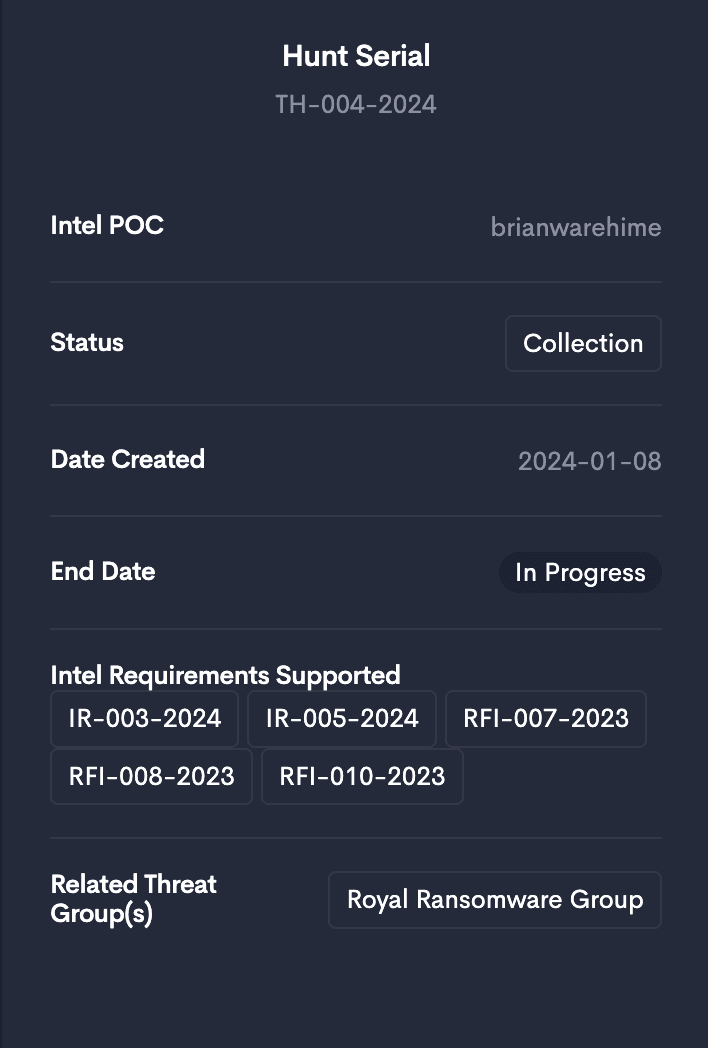
Track Threat Hunting Activity
Manage Intelligence Requirements, Stakeholders, and more..
Beautiful Stakeholder Reporting
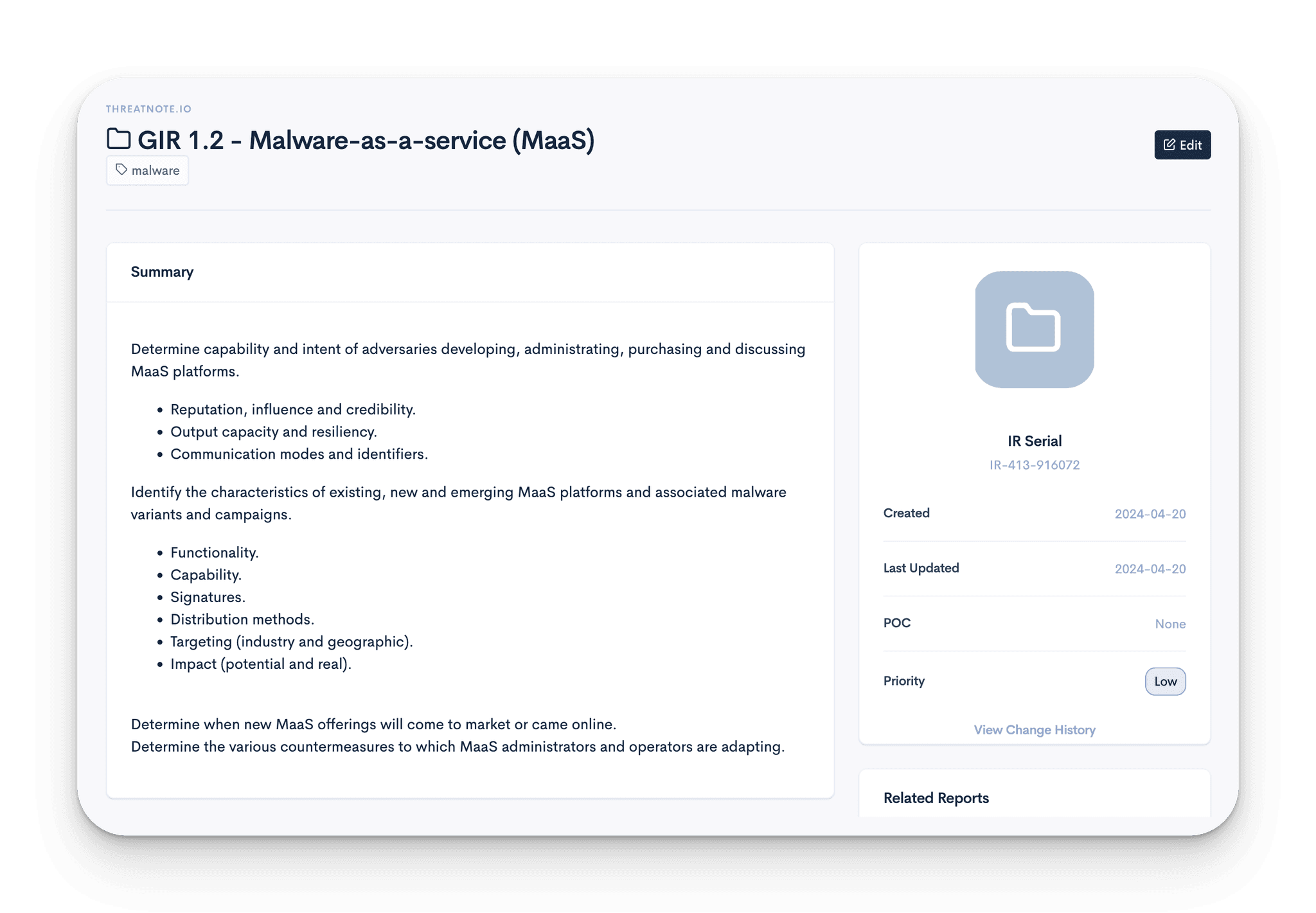
Collection Management Framework
Actor Tracking
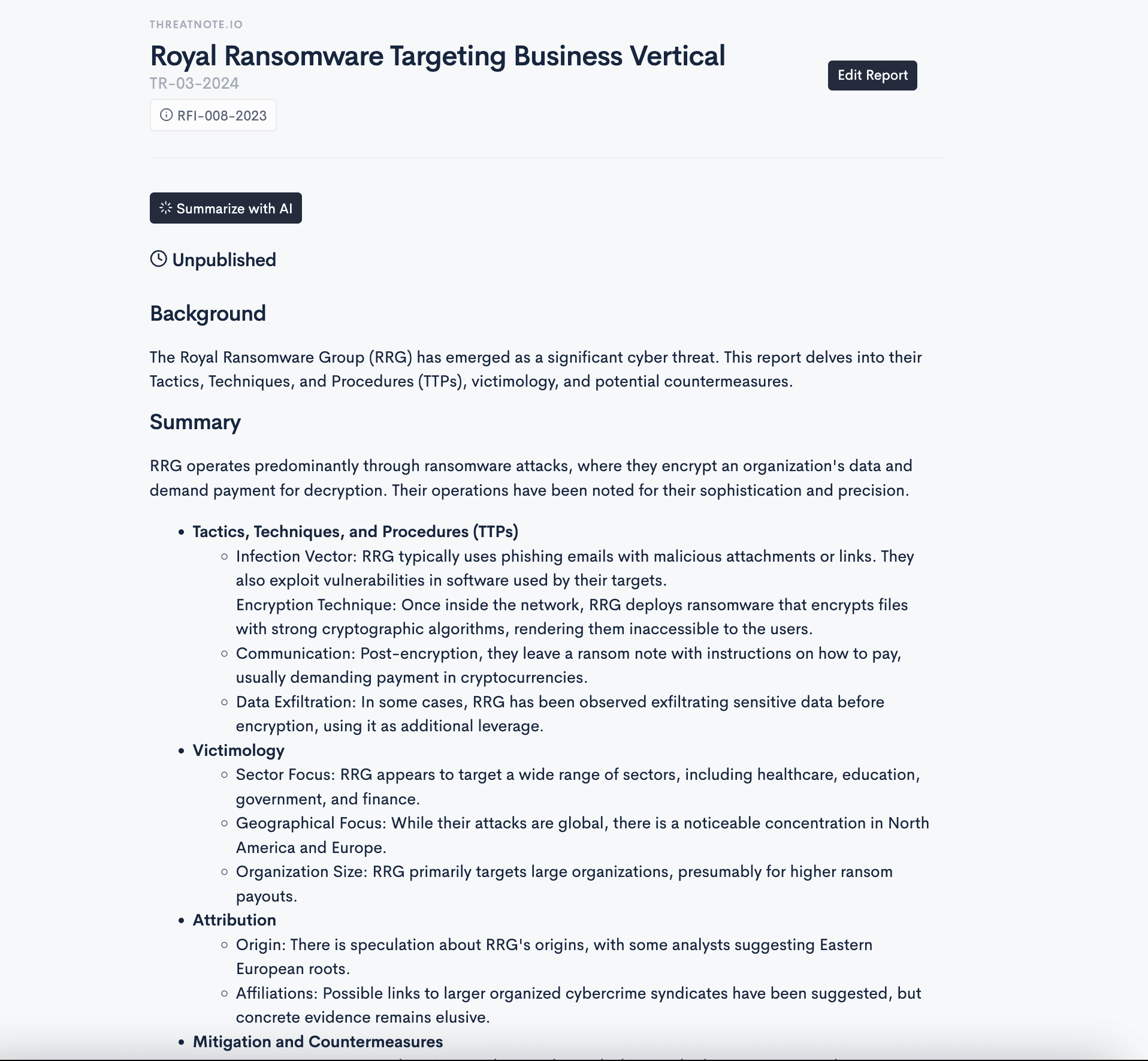
Track threat groups targeting your vertical
Identify and manage MITRE ATT&CK TTP’s
Associate threat hunts with threat groups
Track targeted regions and sectors for analytics
Rule Repository
Manage threat detection rules
Supports YARA, Splunk, Sigma, Snort
Syntax Highlighting
Marketplace
Intel Marketplace for quicker onboarding
Subscribe quickly to common stakeholder requirements, RFI's and Reports
New content added often!
Stay ahead of threats by understanding what other organizations care about
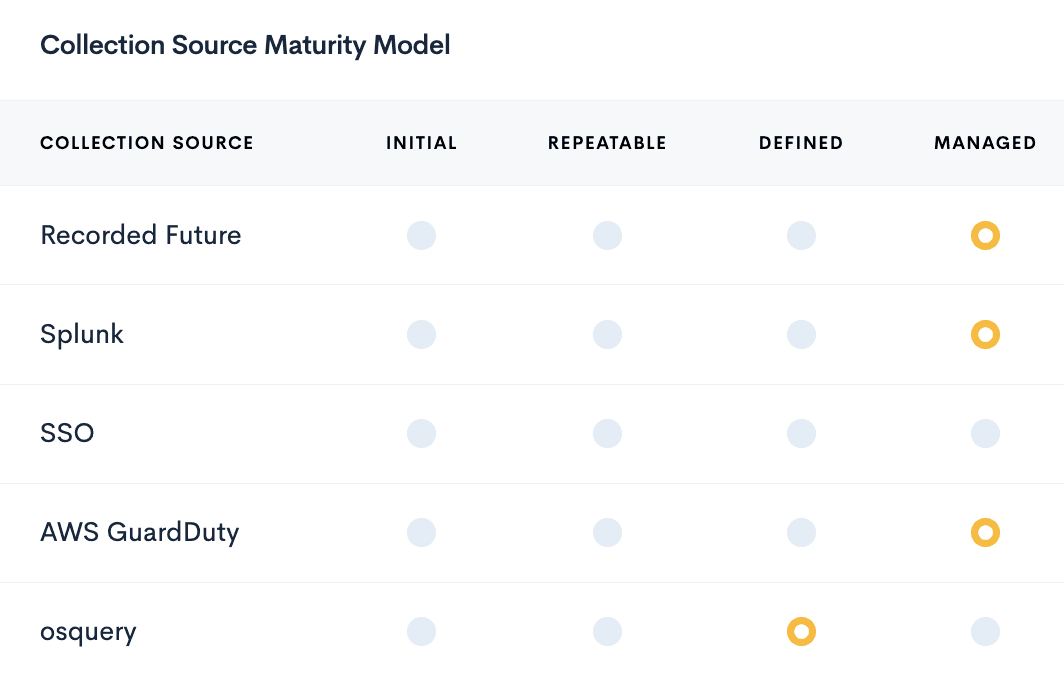
Maturity
Mature your Threat Intelligence Program
Processes and tech in place to instantly level up your maturity level according to the Intelligence Capability Discovery (ICD)
Understand the requirements to improve your teams program, and how to get there.
Streamline Content Dev
With a built-in recommendation library and style guide, make your reporting efforts easier and more efficient.
Understand Your ROI
Gain insightful metrics on your data source ROI to inform purchasing decisions.
Flexible Pricing
Choose the right fit for your business
Need something more? Need a self-hosted version? Contact us at sales@threatnote.io for custom development or pricing. We also offer professional services to get your program up and running, or help you mature your processes.
Our Blog
Take a look at our latest blogs
Enhancing Threat Intelligence Reporting
How to improve intelligence reporting through Threatnote and deliver meaningful content to your customers
Sep 10, 2024
5 Minutes
The Threat Intelligence Lifecycle
What is the Threat Intelligence Lifecycle and how Threatnote Streamlines this Process
Jul 16, 2024
3 min read
Intelligence Requirements
How do you quickly onboard new customers with minimal ramp-up time?
Jan 10, 2024
3 min read